Malicious Software That Can Attack Microsoft Sql Server

New malware created by Chinese-backed Winnti Group has been discovered by researchers at ESET while existence used to proceeds persistence on Microsoft SQL Server (MSSQL) systems.
The new malicious tool dubbed skip-2.0 can exist used by the attackers to backdoor MSSQL Server xi and 12 servers, enabling them to connect to any account on the server using a so-called "magic password" and hide their activeness from the security logs.
"This backstairs allows the attacker not but to gain persistence in the victim'due south MSSQL Server through the utilise of a special password, only also to remain undetected thanks to the multiple log and issue publishing mechanisms that are disabled when that password is used," says ESET researcher Mathieu Tartare.
Winnti Group'southward armory is growing
The Winnti Group is an umbrella term used as the proper noun of a collective of Chinese land-backed hacking groups (tracked equally Blackfly and Suckfly by Symantec, Wicked Panda by CrowdStrike, BARIUM by Microsoft, APT41 by FireEye) sharing the same malicious tools that have been in use since around 2011.
That is when Kaspersky found the hackers' Winnti Trojan on a large number of compromised gaming systems subsequently it got delivered via a game's official update server.
After analyzing the new backdoor, ESET's researchers have as well discovered that skip-two.0 shares some traits with other Winnti Group malware, "in particular, with the PortReuse and ShadowPad backdoors."
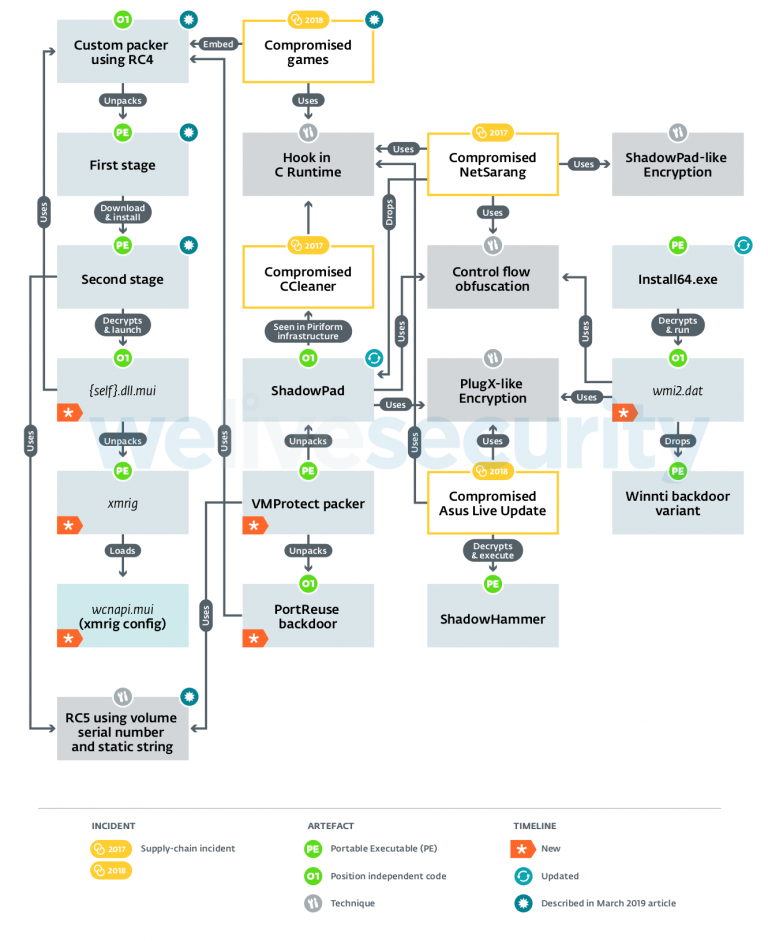
PortReuse, a modular Windows backdoor, was used by the Winnti hackers in an attack targeting the servers of a high-profile Asian mobile software and hardware manufacturer.
Also, PortReuse is "a network implant that injects itself into a process that is already listening on a network port and waits for an incoming magic parcel to trigger the malicious code."
ShadowPad is another Winnti backdoor used by the grouping as part of a supply chain assail from 2022 that impacted NetSarang, a Soth Korean maker of network connectivity solutions, when the hacking group successfully infected the visitor's server management software with the backstairs.
All three backdoors use the same VMProtected launcher and the group's custom malware packer and, to meridian it all off, likewise share multiple other similarities with several other tools associated with the threat grouping's past operations.
MSSQL Server eleven and 12 under set on
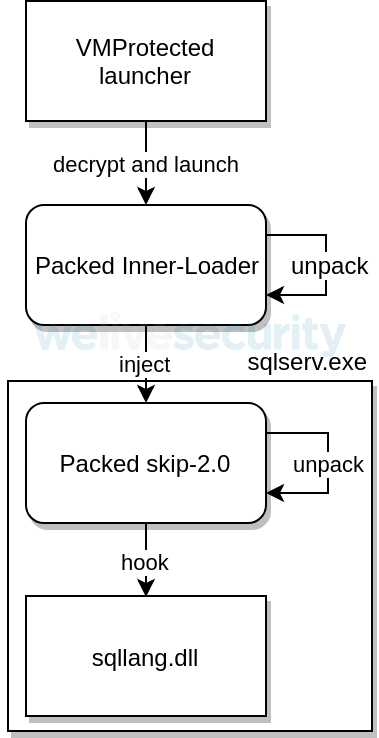
Once dropped on an already compromised MSSQL server, the skip-2.0 backdoor gain to inject its malicious code within the sqlserv.exe process via the sqllang.dll, hooking multiple functions used for logging an authentication.
This allows the malware to bypass the server's congenital-in hallmark machinery and thus allow its operators to log in fifty-fifty though the account password they entered does not match.
"This part'south hook checks whether the countersign provided by the user matches the magic countersign, in that case, the original function volition non be chosen and the hook will render 0, assuasive the connection fifty-fifty though the correct password was not provided," says ESET.
"We tested skip-2.0 confronting multiple MSSQL Server versions and plant that nosotros were able to log in successfully using the special password only with MSSQL Server 11 and 12," Tartare adds.
While MSSQL Server eleven and 12 are not the most recently released versions — they were released in 2012 and 2022 — they are the most common ones according to data ESET's researchers got from Censys.
"The skip-2.0 backdoor is an interesting add-on to the Winnti Grouping'due south arsenal, sharing a great bargain of similarities with the group'due south already known toolset, and allowing the attacker to accomplish persistence on an MSSQL Server," ESET's research team concludes.
"Considering that administrative privileges are required for installing the hooks, skip-2.0 must be used on already compromised MSSQL Servers to achieve persistence and stealthiness."
Source: https://www.bleepingcomputer.com/news/security/chinese-hackers-use-new-malware-to-backdoor-microsoft-sql-servers/
0 Response to "Malicious Software That Can Attack Microsoft Sql Server"
Post a Comment